Designlet: Migrating AWS EC2 Instances into VMware Cloud on AWS using vCenter Converter 6.4
Introduction
With the release of vCenter Converter 6.4, customers can now migrate AWS EC2 instances to VMs on VMware Cloud on AWS SDDCs.
This guide will cover the following:
- Deploying the vCenter Converter Server and Worker services on a VM within a VMware Cloud on AWS SDDC.
- Configuring vCenter Converter Server for use with VMware Cloud on AWS
- Configuring networking and security to enable communications between the Converter Server, source AWS EC2 instances and the VMware Cloud on AWS SDDC. Two means of connecting to AWS EC2 instances will be discussed:
- SDDC Groups: SDDC Groups with Native VPC attachment(s) support higher-speed migrations of EC2 instances in multiple VPCs and AWS accounts into VMware Cloud on AWS. Preferred method.
- Connected VPC: AWS EC2 instances within the VPC connected to your VMware Cloud on AWS SDDC may be migrated without SDDC groups. This method may be easier to setup but has migration performance implications and source VPC placement limitations.
- Walk-through of Linux and Windows EC2 instance conversion
Out of Scope in this Document
- Network security rules, monitoring, and backup reconfiguration for the newly converted VMs.
- OS and application licensing for newly converted VMs.
- Other means of connecting to EC2 instances such as via EIP.
Summary and Considerations
| Use Case | Migrating Windows and Linux EC2 instance to VMware Cloud on AWS using vCenter Converter |
| Application Considerations |
|
| Pre-requisites |
|
| Performance Considerations | Utilizing SDDC Groups will significantly improve the performance of your migrations as the alternative, “proxy mode” (required for Connected VPC based migrations) sufficiently reduces data transfer performance. Note that the improved performance comes at a cost: SDDC group traffic, even in the same AZ, is metered. To migrate more than twelve EC2 instances concurrently into VMware Cloud on AWS, multiple vCenter Converter Servers are required. Consider lowering this limit if you see excessive timeouts or failures (documentation). Performance of the vCenter Converter server is best when using a VMXNET3 network adapter (documentation). |
| Network Considerations/Recommendations | Every AWS network configuration is different, so some variation of the networking and routing configuration may be required. |
| Cost Implications | Exporting data from EC2 will often incur egress network fees. Please review the following AWS data transfer pricing pages for more information. Importing large amounts of data (AWS EC2 instances) into a VMware Cloud on AWS SDDC may trigger eDRS to add more hosts. |
| Document Reference | Configuring VMware Cloud on AWS Networking and Security Using NSX Creating and Managing SDDC Deployment Groups with VMware Transit Connect™ |
| Last Updated | May 12, 2023 |
Background
vCenter Converter 6.4 supports a new cloud source (AWS EC2 instances) and a cloud target (VMware Cloud on AWS). Connecting these platforms requires network and security configuration on the VMware Cloud and AWS platforms and advanced reconfiguration of the vCenter Converter service.
Converter Server and Networking Setup
Deployment and Configuration of vCenter Converter Server
Deploy a dedicated Windows VM inside your VMware Cloud on AWS SDDC (Compatible OSs).
Ensure the VM uses a “VMXNET3” para-virtualized network adapter for optimal performance.
Once your VM is ready, download, and launch the vCenter Standalone Converter installer.
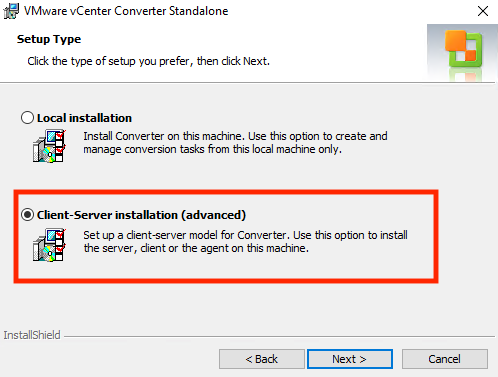
Select “Client-Server Installation (advanced)” to install only the necessary components.
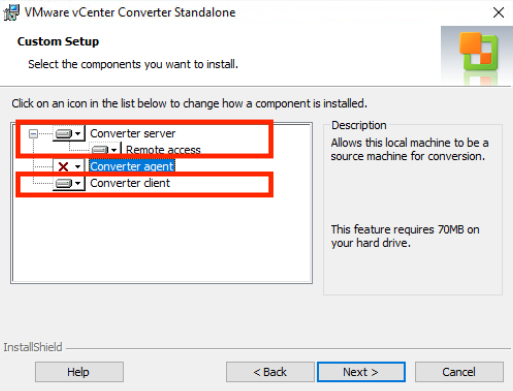
Unselect “Converter Agent” (as this VM is already in VMware Cloud on AWS) and ensure both “Converter server” and “Converter client” remain selected.
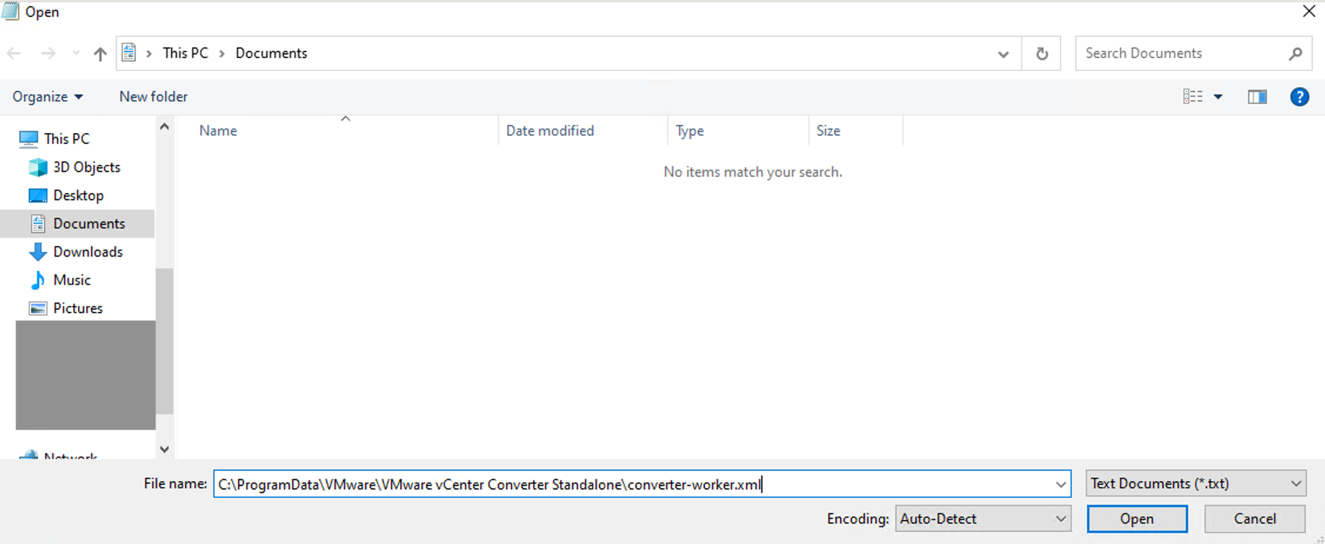
After the installation is complete, we need to update an advanced setting that allows vCenter Converter Server to communicate with VMware Cloud on AWS ESX hosts by IP address. Without this configuration change, you will be unable to convert Linux EC2 instances to VMware Cloud on AWS-based Linux VMs.
- Use notepad to open C:\ProgramData\VMware\VMware vCenter Converter Standalone\converter-worker.xml
- Find the line <UseHostIPForWebSocketTicket>false</UseHostIPForWebSocketTicket>
- Change the value “false” to “true.”
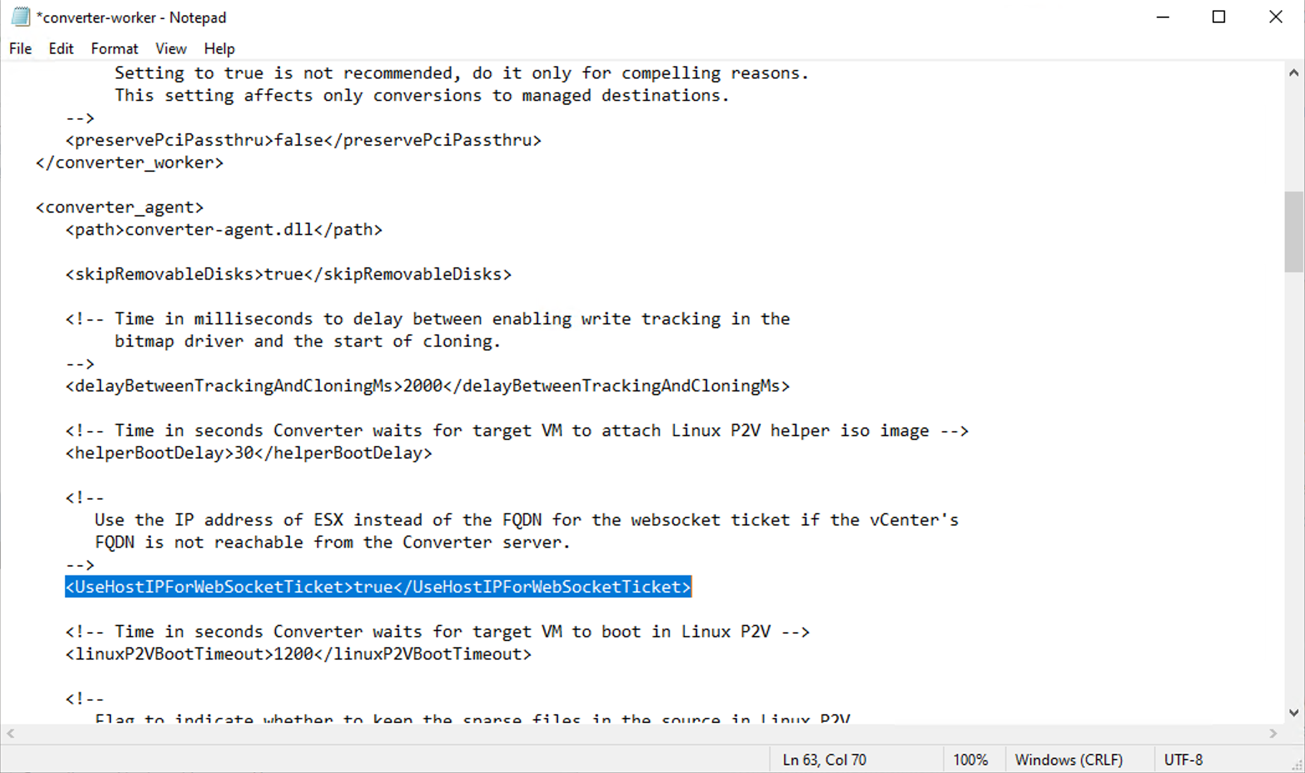
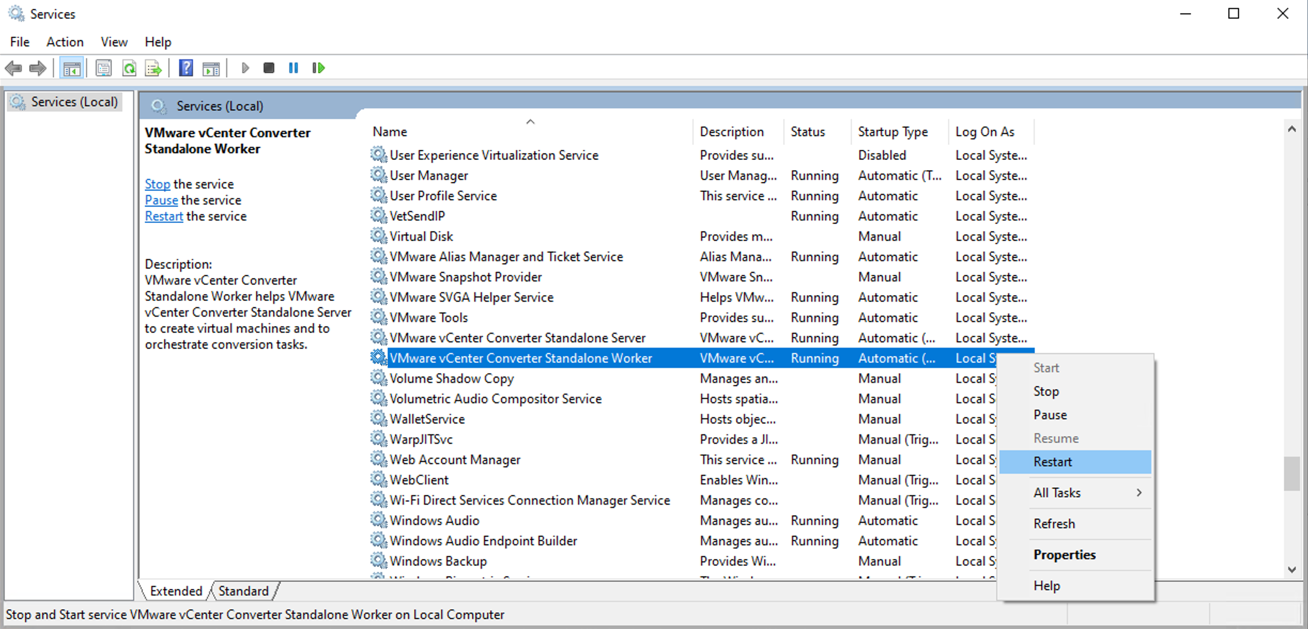
- Save the file and restart the “VMware vCenter Converter Standalone Worker” service.
Networking and Security Configuration
- This setup will be different depending on whether you choose the Connected VPC or SDDC Groups path.
Choosing your network path:
| Path | AWS VPC Limitations? | Chargeable Traffic | Performance |
| Connected VPC | Connected VPC only | No charge for traffic in the same AZ | Medium |
| SDDC Groups | Any VPC attached to the vTGW in the SDDC Group | All traffic | High |
VMware Cloud on AWS Network and Security Configuration
Common Setup - Firewall
These steps will ensure that the vCenter Converter VM can connect to both ESX and vCenter to orchestrate the migration.
- Create a Management Group called Converter Server containing the private IPv4 Address of the Converter Server.
- Create a Management Group called EC2-Subnets containing the subnet ranges for the EC2 Windows servers you wish to convert.
- Create a Management Firewall rule with source Converter Server and source EC2-subnet, destination vCenter, and Services HTTPS. Ensure the rule is set to Allow.
- Create a Management Firewall rule with source Converter Server, destination ESX, and Services HTTPS and Provisioning and Remote Console. Ensure the rule is set to Allow.
- Create a Compute Group containing the Converter Server VM
- Add a Compute Gateway rule allowing the Converter Server to connect to any. For those with more stringent firewall requirements: minimally, Converter Server must connect to the SDDC infrastructure management range and the AWS subnet range.
Common Setup – Network Segment Configuration
- Ensure you have a routed network segment for the converted VMs that is configured to provide IP addresses via DHCP (documentation). Please note the network range (ex: 192.168.1.100.0/24) and network name for later use.
- Ensure the network segment for converted VMs and the vCenter Converter Server VM have direct outbound access. If the Converter Server VM does not have Internet access, please configure vCenter Converter Server service without the Customer Experience Improvement Program (CEIP) option enabled. Granular outbound firewalls rules are beyond the scope of this document.
Connected VPC Specific Setup
No other configuration is required on the VMware Cloud on AWS network side.
SDDC Group Setup
Create (or modify existing) an SDDC Group containing the SDDC which you will be importing AWS EC2 instances into (documentation)
- Attach the native AWS VPC(s) that contain your AWS EC2 instances (documentation).
- Modify the SDDC group’s External VPC attachment(s) to include the AWS network CIDR ranges of the AWS EC2 instances which are eligible for migration.
AWS Network and Security Configuration
Common Setup – Security Group Configuration
- Add or confirm the following entries are in the security groups attached to the EC2 instances in question.
Inbound rules:
- A source of the private IP of vCenter Converter Server and destination port of TCP/9089
- A source of the private IP of vCenter Converter Server and destination port of TCP/22
- A source of subnet range of the converted VM network and destination port of TCP/22
If you only intend to migrate Windows VMs, you may elide rules 2 and 3. If you only intend to migrate Linux instances, you may elide rule 1.
Outbound rule:
Ensure the default Security Group (SG) outbound rule is present, allowing all traffic to all destinations.
While more granular rules are possible, they are out of scope for this document.
Connected VPC Specific Setup
Verify the default VPC security group (SG) has an allow any outbound rule. This is the default, and thus should only be missing if purposefully modified.
SDDC Groups Specific Setup
- Identify the route table(s) for the subnet(s) your EC2 instance(s) belong to.
- Modify them to include three networks, each one with the TGW attachment associated with your VMware vTGW as the target. To do so, type “tgw-” in the target box and it will populate the list with the description. Select the one for the SDDC group in question).
- Network for Converted VMs
- Network vCenter Converter Server resides on
- Infrastructure network for SDDC
Preparing AWS EC2 instances for Conversion
- Review the list of supported Source OSs by looking at the “Source for Powered On Machine Conversions” column in the vCenter Converter release notes.
- Verify that you have administrative access to the systems due to be converted. Converter Server can utilize a non-root user on Linux VMs if said user has full sudo rights.
Installing Converter Agent on AWS EC2 Windows Instance
This process (an automated equivalent, using a service like SCCM) must be repeated for each AWS EC2 instance due to be converted.
- Using Remote Desktop (RDP) connect to the AWS EC2 Instance
- Download (or otherwise transfer the unified installer to) your EC2 instance.
- Launch the vCenter Standalone Converter installer.
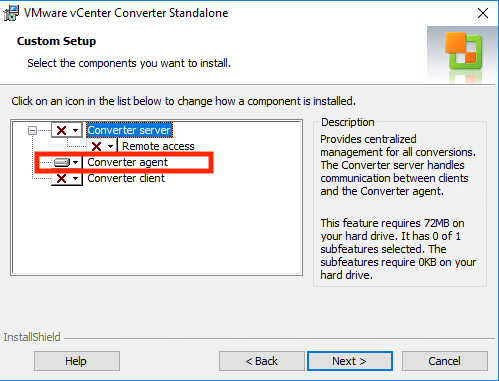
- Select “Client-Server Installation (advanced)”

- Select only the Converter agent (Converter server and Converter client should be de-selected).
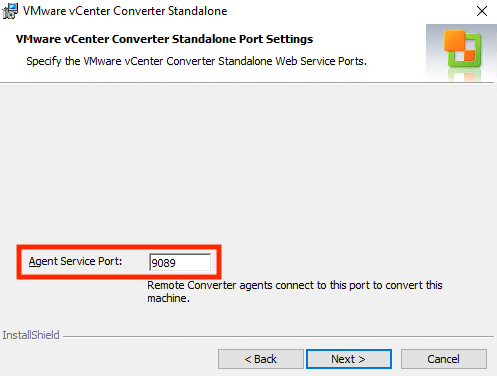
- The default agent port (by which the Converter Server running in VMware Cloud on AWS communicates with the AWS EC2 Windows instance) is TCP/9089. For this document's purposes, we will leave this as default.
Sample Conversion Process for a Linux and Windows EC2 instance
- Using Remote Desktop (RDP) connect to your Windows Converter Server VM
- Launch the VMware vCenter Converter Standalone Client
- Choose “Connect to local server.”
- Click on “Convert Machine.”
- Choose either “Remote Windows machine” or “Remote Linux machine” (as appropriate).
- For Windows systems:
- If the vCenter Converter agent was set up with something other than the default listener (TCP/9089) you must specify the port in the “IP address or name” input field. For example: 192.168.1.10:443. If you utilized the default listener port, you may elide the port number (ex: 192.168.1.10)
- Authentication is username/password only.
- For Linux systems:
- If your Linux system is using a non-standard SSH server port (something other than TCP/22 you must specify the port in the “IP address or name” input field. For example: 192.168.1.10:2222. If you utilized the standard SSH server port, you may elide the port number (ex: 192.168.1.10)
- Authentication is username/password or username plus private key (with optional passphrase). Please be mindful of any security implications if you choose to copy your private SSH key for your EC2 instance to this system.
- Select VMware Infrastructure Virtual Machine as the destination type.
- Enter your SDDC vCenter’s fully qualified domain name (for example: vcenter.sddc-A-B-C-D.vmwarevmc.com), username (ex: cloudadmin@vmc.local), and password.
- If you are using Connected VPC method, you must select proxy mode.
- If you are using the SDDC Groups method, do not select proxy mode.
- When configuring the destination for your pending converted VM, be mindful to select only resources you have access to (ex: Workload Datastore and Workloads folder) to avoid permission errors.
- Review the virtual hardware properties of the pending converted VM to ensure it uses the converted VM network established in an earlier setup.
Note: the migration process does not shut down the source EC2 VM.
Post conversion:
- Validate the converted VM.
- Install VMware Tools
- Shutdown the source EC2 instance and direct any applications to the new VM.
Authors and Contributors
- Author:
- Nathan Thaler, Staff II Product Solutions Architect, Cloud Infrastructure Business Group
- Contributors:
- Michael Kolos, Technical Product Manager, Cloud Infrastructure Business Group
- William Lam, Senior Staff Product Solutions Architect, Cloud Infrastructure Business Group
- Rohit Parashar, Senior Member of Technical Staff, Cloud Infrastructure Business Group
- Plamen Doykov, Staff Engineer, Cloud Infrastructure Business Group
