Add Google Cloud VMware Engine IAM Role to Authenticate from Compute Engine with gcloud CLI
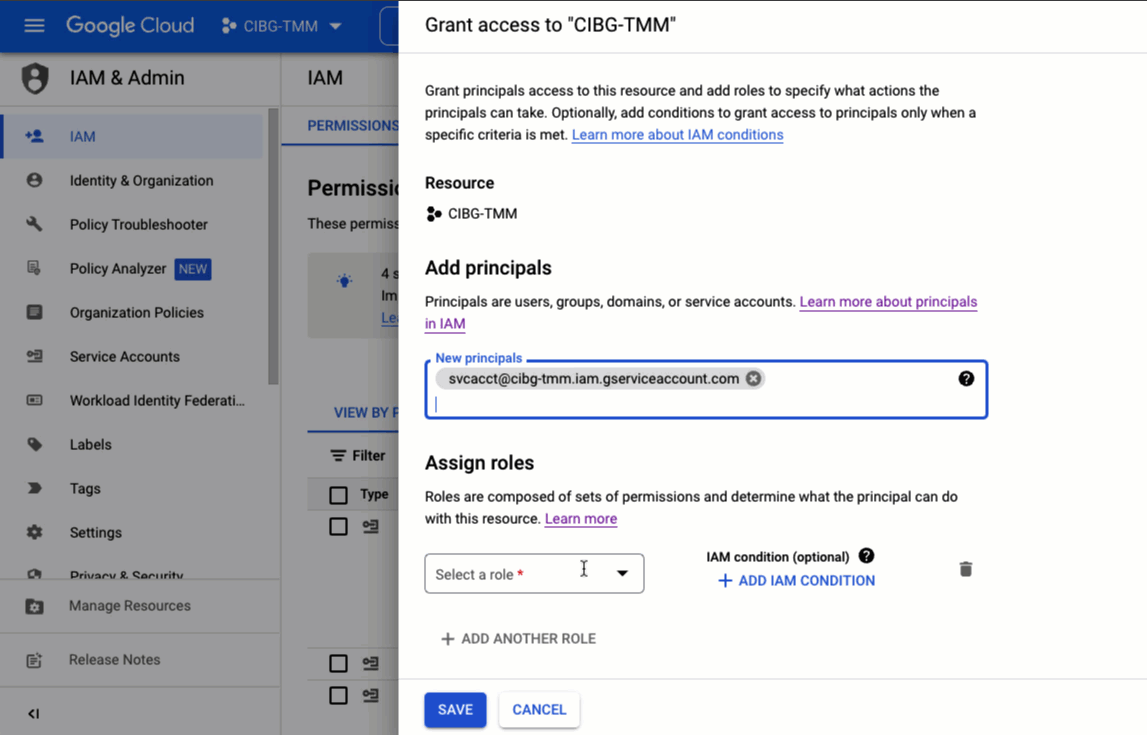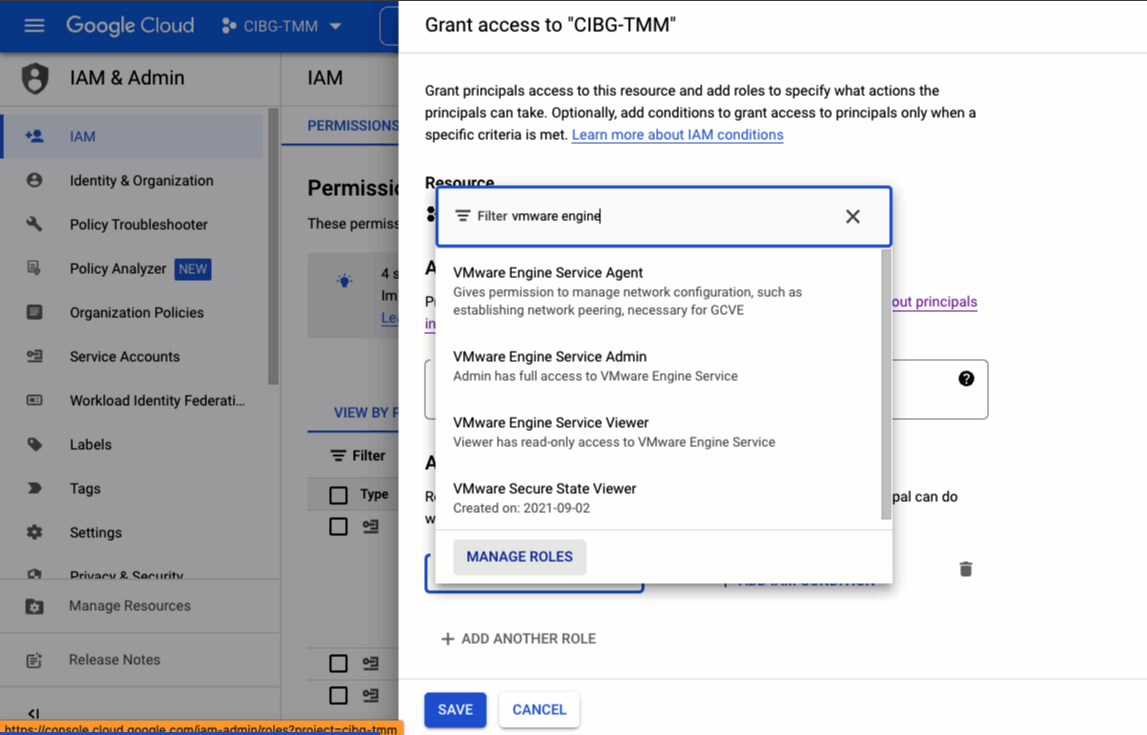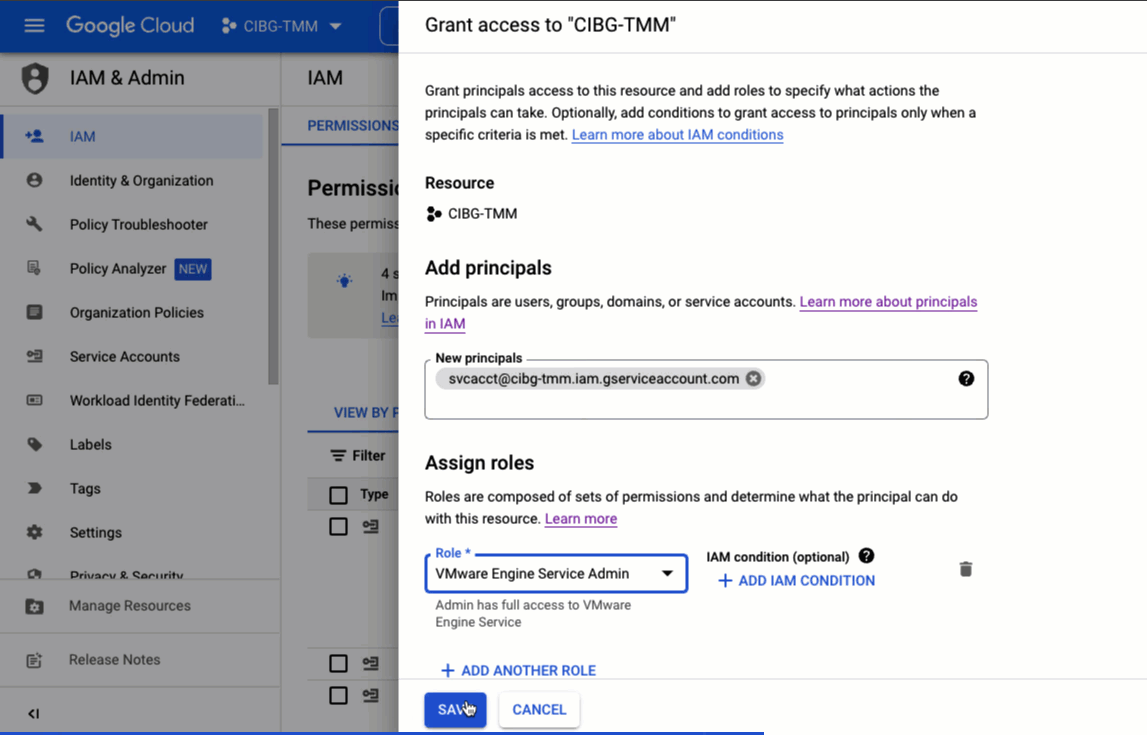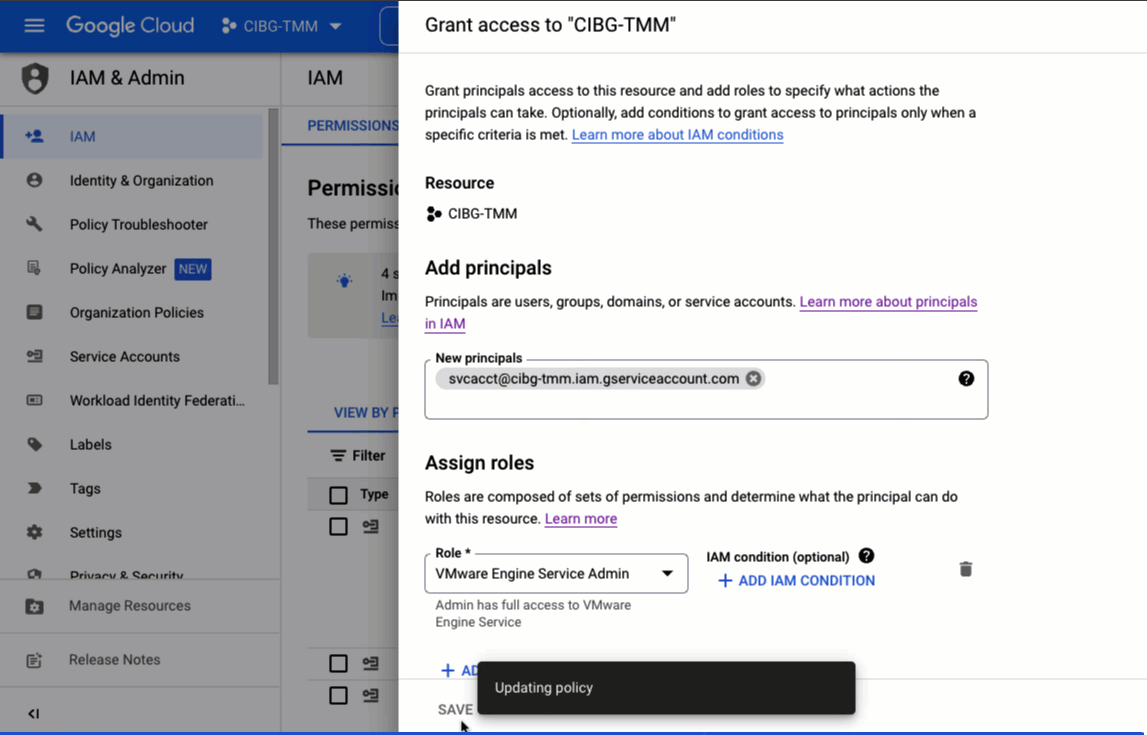
Google Cloud Platform uses Identity and Access Management (IAM) to centrally control access to resources. In order to use the gcloud CLI to manage Google Cloud VMware Engine, an appropriate IAM role must be assigned to a principal, which could be a user account or service account.
Currently there are three VMware Engine IAM roles: agent, admin, and viewer. The agent role is intended for configuring networking and peering for the private cloud. The admin can manage the private cloud configuration and the viewer is a read-only role that cannot make changes.
To assign a role to an IAM principal, you can use the Google Cloud console GUI, as shown below, or the gcloud CLI.

Principal Principles
You may be wondering about principals, and which one needs to be granted the necessary IAM roles to accomplish a particular task. There are a number of different types of principals, but in the case of accessing Google Cloud VMware Engine, the principal will typically be either your own user account or a service account that is associated with a Compute Engine instance. If you initialize the gcloud CLI on your laptop then you will be using your own user account for access, but if you're running gcloud from inside a GCE VM, the corresponding service account would be the relevant principal.
See it in Action
To help with troubleshooting, below is a simple script that creates a new service account, assigns the VMware Engine Admin role to it, and then launches a new GCE instance running with that service account. If you log into the VM, you are able to use the gcloud CLI with that service account principal to access your GCVE private cloud configuration.

![]()
#!/usr/bin/env bash
# 10Jan2023 - Eric Gray
# Simple script to quickly create a GCE instance with IAM role for GCVE
SVC_ACCT_NAME=${SVC_ACCT_NAME:-gce-to-gcve}
NEW_INSTANCE=${NEW_INSTANCE:-automation-vm}
ZONE=${ZONE:-us-west2-a}
PROJECT_ID="cibg-tmm"
IAM_ROLES="roles/vmwareengine.vmwareengineAdmin roles/storage.admin roles/compute.admin"
gcloud iam service-accounts create "$SVC_ACCT_NAME" --format=json
svc_acct="${SVC_ACCT_NAME}@${PROJECT_ID}.iam.gserviceaccount.com"
for i in $IAM_ROLES ; do
gcloud projects add-iam-policy-binding $PROJECT_ID \
--member="serviceAccount:${svc_acct}" --role="$i" 1>/dev/null
done
subnet=$(gcloud compute networks subnets list \
--regions="${ZONE%-a}" --format="value(selfLink.basename())")
gcloud compute instances create "$NEW_INSTANCE" \
--zone="$ZONE" --subnet="$subnet" \
--machine-type=e2-micro \
--image-project=ubuntu-os-cloud --image-family=ubuntu-2204-lts \
--scopes=cloud-platform --service-account="$svc_acct"
Takeaway
Security is a critical aspect of public cloud computing and understanding how to control access with roles and permissions is an important responsibility for administrators. Whenever possible, use a predefined or custom role to assign the fewest permissions required for users and applications in order to limit the impact of potential breaches.
