Configure Conditional DNS forwarding between OCI and AD Domain
Introduction
DNS is undoubtedly one of the critical functions in the IT infrastructure. Given the current trends, organizations are deploying and managing IT environments across multiple clouds spanning geo-locations. This multi-cloud deployment requires a robust DNS query resolution mechanism that can simplify DNS resolution across distributed environments. One such mechanism and, I guess, historically well-adopted mechanism is the DNS forwarding that allows you to create forwarding rules based on specific Domain or CIDR requests. This document will walk you through the steps on how to implement DNS forwarding between OCI and AD domain DNS servers.
Oracle Cloud VMware Solution is deployed in Oracle Cloud Infrastructure regions and uses the native OCI DNS service. It leverages OCI DNS service to obtain and resolve the name resolution queries for the OCVS VMware SDDC appliances and OCI endpoints. Once the VMware SDDC is up and running, you can onboard OCVS VMware SDDC appliances and application workloads to the organization's DNS Servers. This will allow you to query your existing organization's AD domain and resolve the VMware SDDC appliance’s DNS queries for specific use cases. These use cases can be configuring VMware SRM, VMware Tanzu, and VMware Horizon or resolving application endpoints within the native OCI cloud and vice versa. To achieve this task, we will use one of the DNS features, Conditional DNS forwarding. In this how-to guide, I will walk you through the steps and important details about configuring conditional DNS forwarding between the OCI DNS service and the active directory DNS server.
Below are some key objectives we will achieve with this implementation guide.
- Ability to resolve OCI endpoints with the clients deployed in OCVS VMware SDDC.
- Ability to resolve application workloads deployed in OCVS VMware SDDC.
- Ability to resolve OCI Endpoints, OCVS VMware SDDC workloads (VMs), and On-prem workloads.
Scope of the Document
This document requires a basic understanding of DNS, VMware SDDC, and Oracle Cloud Infrastructure.
Summary and Considerations
| Use Case | Resolving DNS queries within the OCI, OCVS VMware SDDC workloads, and on-prem environment. |
| Pre-requisites | Below are some of the pre-requisites to configuring conditional DNS forwarder:
|
| General Considerations/Recommendations |
|
| Performance Considerations | There are no specific performance considerations except creating a separate subnet in OCI to host DNS endpoints. Also, it ensures that all the DNS servers in the AD domain are healthy. |
| Network Considerations/Recommendations |
|
| Document Reference | |
| Last Updated | January 2023 |
What is conditional DNS forwarding?
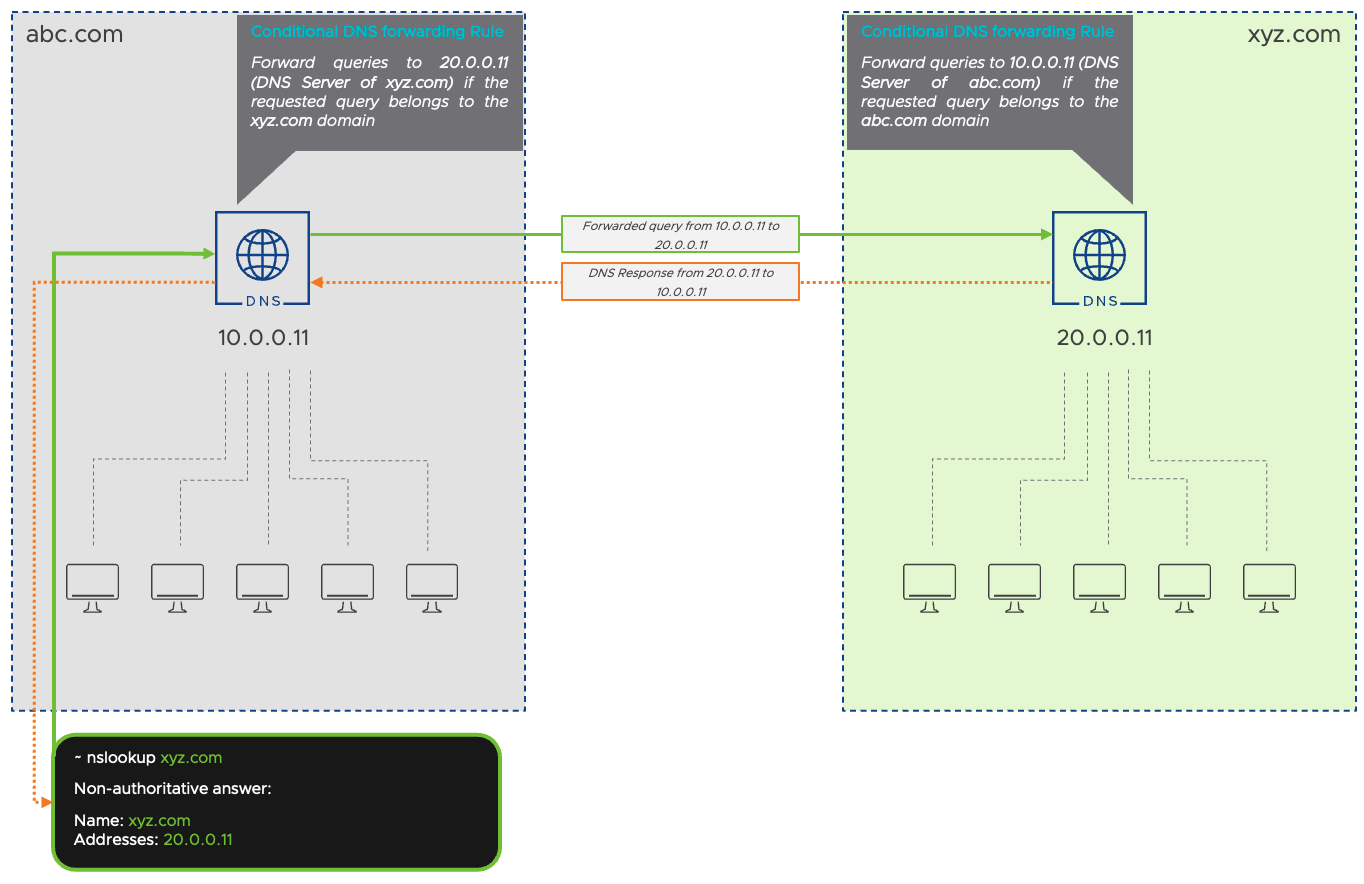
Conditional DNS forwarding is a method to direct DNS queries related to a specific domain to another DNS server. This is done by creating conditional DNS forwarders or rules on the DNS server. This is a simple and reliable method to resolve DNS queries belonging to an external domain.
For example, as illustrated in the above diagram, we have two domains, abc.com and xyz.com. Clients belonging to abc.com reach out to their DNS server, which is 10.0.0.11. Similarly, clients belonging to xyz.com reaches out to their DNS server, which is 20.0.0.11. However, in a scenario where clients from the abc.com domain will not be able to resolve queries related to xyz.com because it does not have any DNS records of the xyz.com domain and vice versa.
To resolve this issue, you can configure a conditional DNS forwarder to point external DNS server to resolve queries belonging to a specific domain. This DNS server is expected to have the DNS records of the requested domain.
As shown in the above diagram, a conditional DNS forwarder is configured on the abc.com DNS server that can be understood as “Forward queries from abc.com to 20.0.0.11 (DNS Server of xyz.com) if requested query belongs to the xyz.com domain”. Similarly, a conditional DNS forwarder is configured on the abc.com DNS server that can be understood as “Forward queries from xyz.com to 10.0.0.11 (DNS Server of abc.com) if requested query belongs to the abc.com domain”.
Implementation
In the below section, we will look at the implementation steps to configure conditional DNS forwarding between the OCI DNS endpoint and our custom AD domain.
Before you begin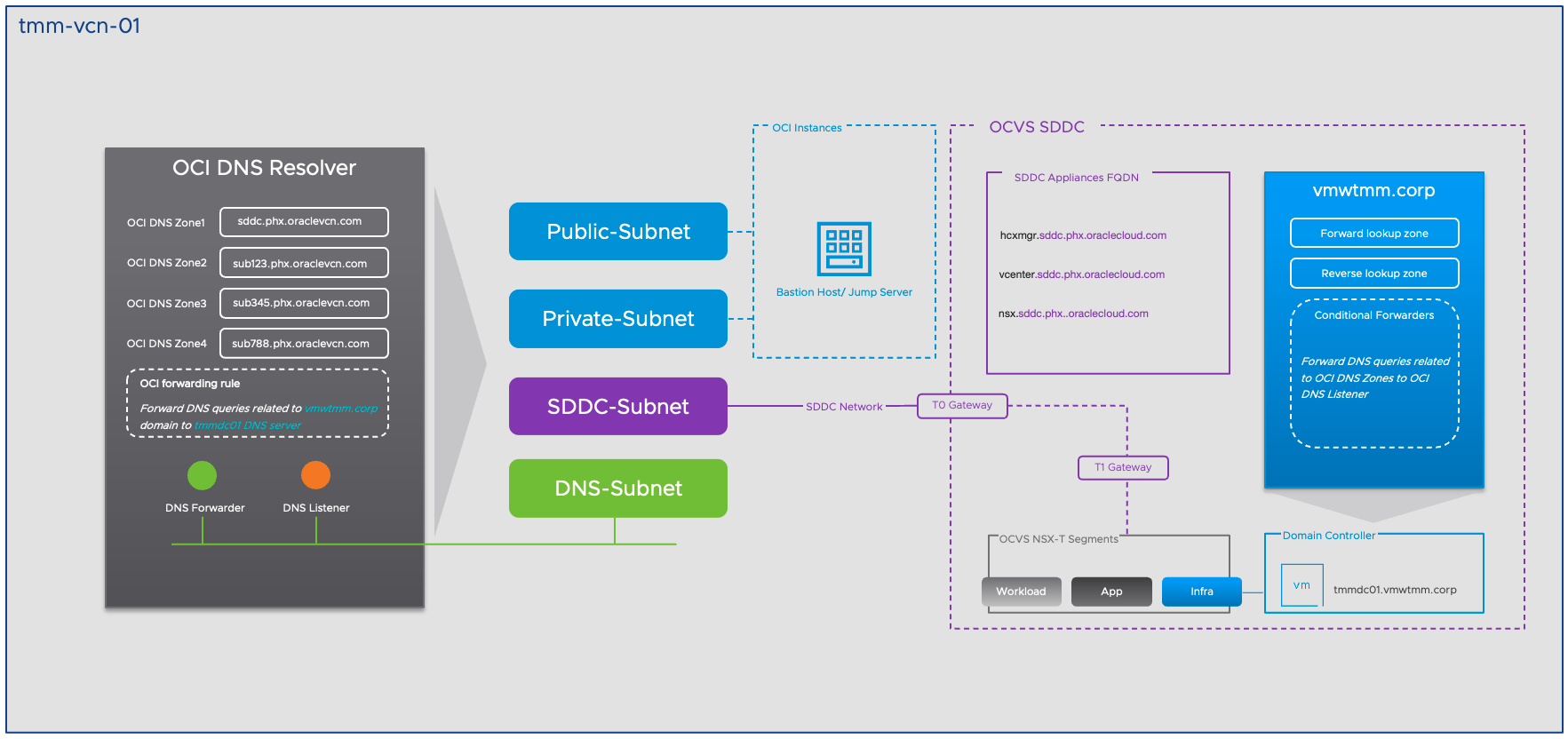
Before we begin the implementation, let us quickly understand the setup. The OCVS is a native tenant of OCI and leverages OCI infrastructure for compute, networks, and storage. I assume you do have a basic understanding of OCVS networking, so I will not touch base on all the details related to OCVS networking. However, I will explain how OCI DNS is playing its role in the OCVS SDDC environment.
Subnets, subnets are logical networks that you can create within the VCN. There can be two types of subnets: public and private.
DNS Resolver, Each VCN has its default OCI DNS resolver. The OCI DNS resolver associates a respective DNS private zone for each subnet in the VCN. All the instances in the OCI point to DNS resolver as their DNS server endpoint. The default DNS server IP address is hidden from the users, and we eventually get a masked IP address when we query the DNS server endpoint.

OCI DNS Zones, As illustrated in the below diagram, we have four subnets: Public, Private, SDDC subnets, and a new DNS subnet (Need to create manually as a part of the implementation step). Each of these subnets has its own DNS zone to keep the DNS records documented.
SDDC DNS Zone, a separate OCI DNS zone, is created when we deploy a new OCVS SDDC. This zone contains the DNS records for all the VMware SDDC appliances. Also, a new separate OCI DNS zone is created to store the ESXi host's DNS records.
OCI DNS Endpoint, The OCI DNS resolver masks its IP address for security reasons. So, if you want to interact with OCI DNS resolver, you must create two DNS endpoints, a DNS forwarder and a DNS listener. Both of these DNS endpoints have a network interface with which other services can communicate.
Task 1: Setup OCI DNS endpoint
As explained in the earlier section, ‘DNS Resolver’, the DNS resolver hides its IPv4 interface for security reasons. To interact with the DNS resolver, you must create DNS endpoints. There are two types of DNS endpoints that you will need to configure. These two DNS endpoints are the DNS forwarder and DNS listener.
Depending on the DNS forwarding rule, the DNS forwarder will be used to forward DNS queries to an external DNS server. Similarly, the DNS listener will be used to receive DNS queries from an external domain. Below are the implementation steps for creating DNS endpoints.
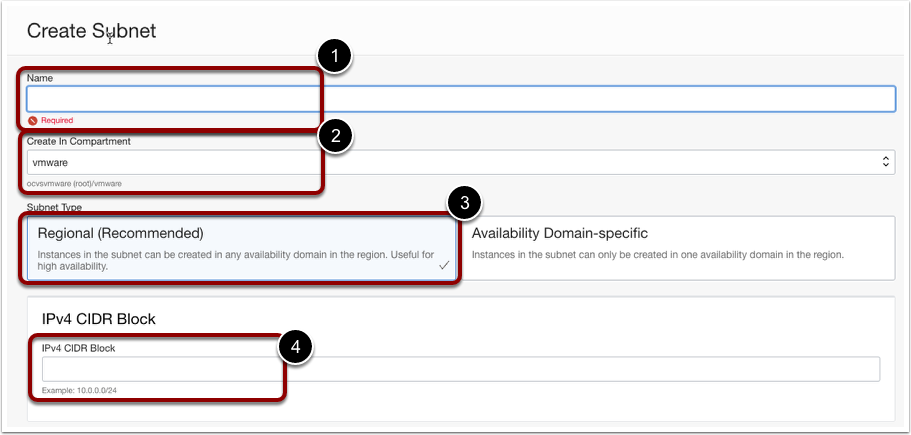
CREATE A NEW SUBNET
Create a new private subnet to host DNS endpoint IP interfaces. This is not mandatory, and you can use any existing private subnet within the VCN, but it is highly recommended to create a new subnet for DNS management to simplify the network management.
- Login to OCI console.
- Click on the Hamburger menu on the top left side.
- Go to Networking and Select Virtual Cloud Network.
- Select the appropriate VCN.
- Scroll down to the Subnet Section.
- Click Create Subnet.
- Provide the following details.
- Subnet name.
- Select the appropriate compartment.
- Select Subnet Type, and Select this as Regional (Recommended)
- Select the IPv4 block. Make sure you pick a CIDR block from the VCN CIDR block and ensure that it does not override with any other CIDR block in your environment.
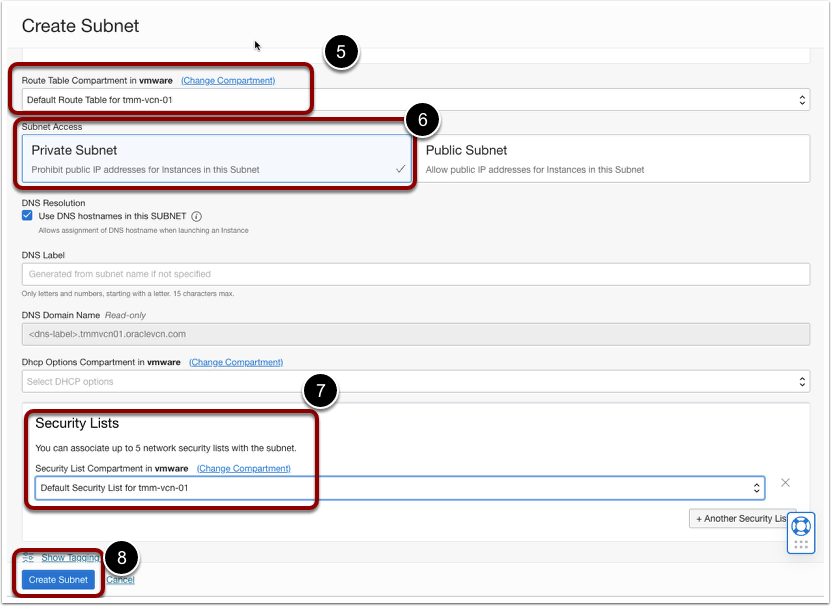
- Select the appropriate route table.
- Select the Subnet access as Private Subnet.
- Keep the ‘Use DNS hostnames in this subnet’ check box enabled under DNS resolution section.
- Select the appropriate security rule.
- Click Create Subnet.
Note: Configure the appropriate route table and security list to enable communication between the OCI DNS subnet and the OCVS custom DNS server. Ensure you can telnet to port 53 in both directions.
CREATE DNS ENDPOINT
Create DNS forwarder and DNS listener on OCI DNS resolver.
- Select the appropriate VCN.
- Click DNS Resolver.
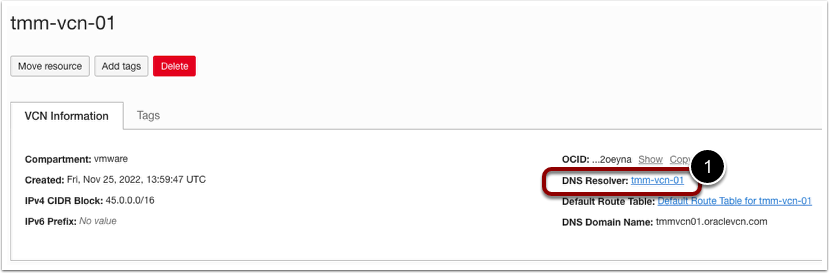
- Under the resources section. Click on Endpoints.
- Click on Create Endpoint.
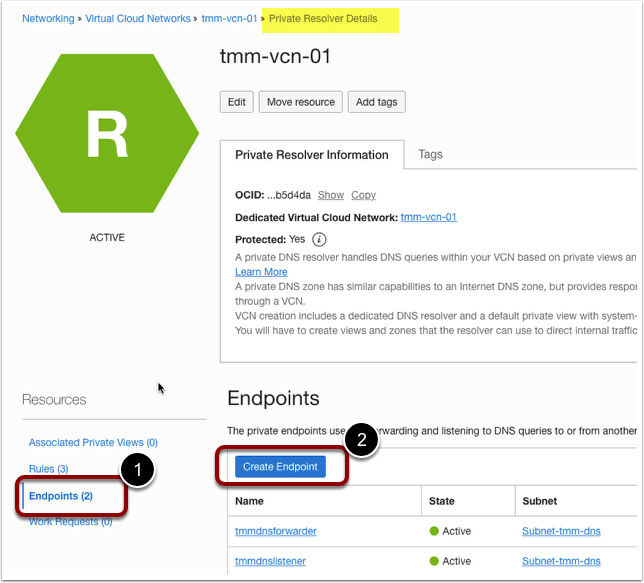
- Create DNS Listener.
- Provide a friendly name.
- Select the Subnet.
- Select the Endpoint type and Select Listening.
- Provide a Listening IP address.
- Create Endpoint.
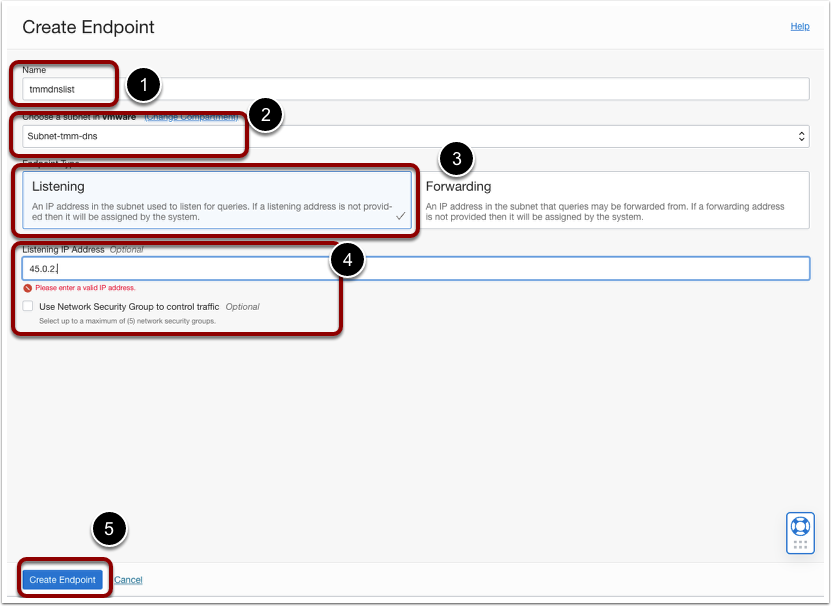
- Create a DNS forwarder.
- Provide a friendly name.
- Select the Subnet.
- Select the Endpoint type and Select Forwarding.
- Provide a Forwarding IP address.
- Create Endpoint.
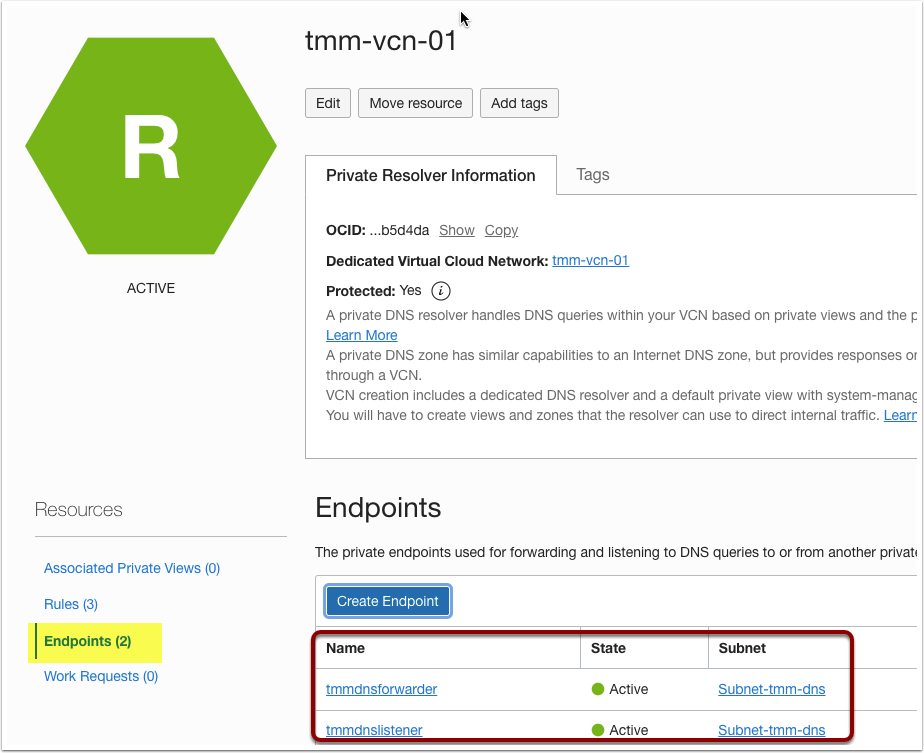
After the successful creation of both endpoints, you should be able to see the endpoint list as below.
Task 2: Create DNS forwarding rules in OCI
Now we have DNS endpoints that can act as the interface to communicate with OCI DNS resolver. In the OCI DNS resolver, create a new DNS forwarding rule to forward DNS queries that belongs to your custom domain to an external DNS server. This will allow OCI instances to resolve DNS queries that belong to your custom domain.
- Go to the DNS resolver.
- Under Resources Section, Click on Rules.
- Click Manage Rule.
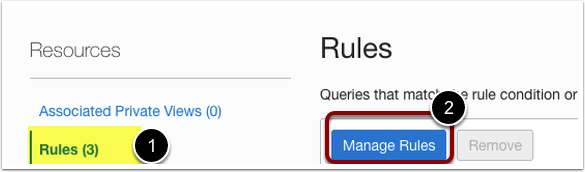
- Provide Rule Condition, Select Domain.
- Provide Domain Name.
- Select DNS Forwarder as the source endpoint.
- Enter the Destination IP address. This is the custom DNS Server IP address in the OCVS environment.
- Click Save Changes.
After the successful completion of this task, you should be able to resolve DNS queries from OCI instances to the custom domain deployed in the OCVS environment.
Task 3: Configure Conditional DNS forwarders in AD DNS Server
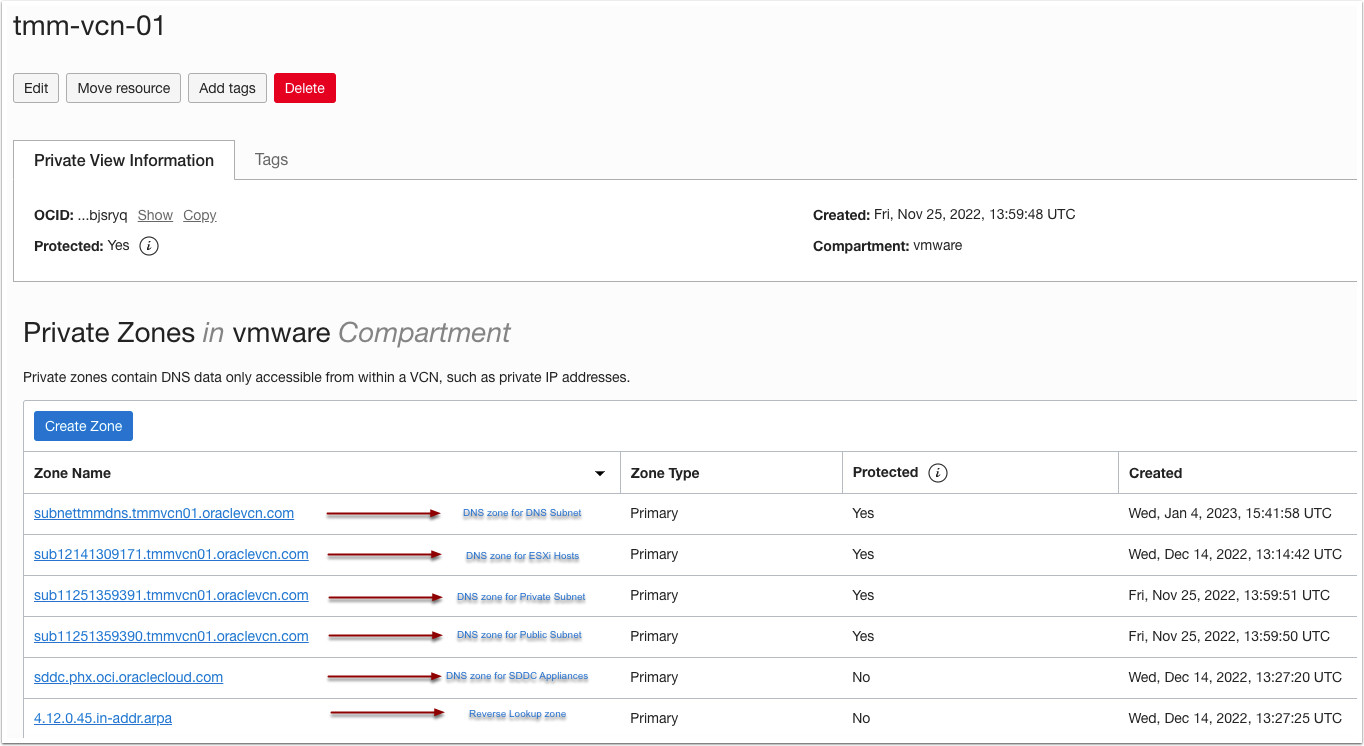
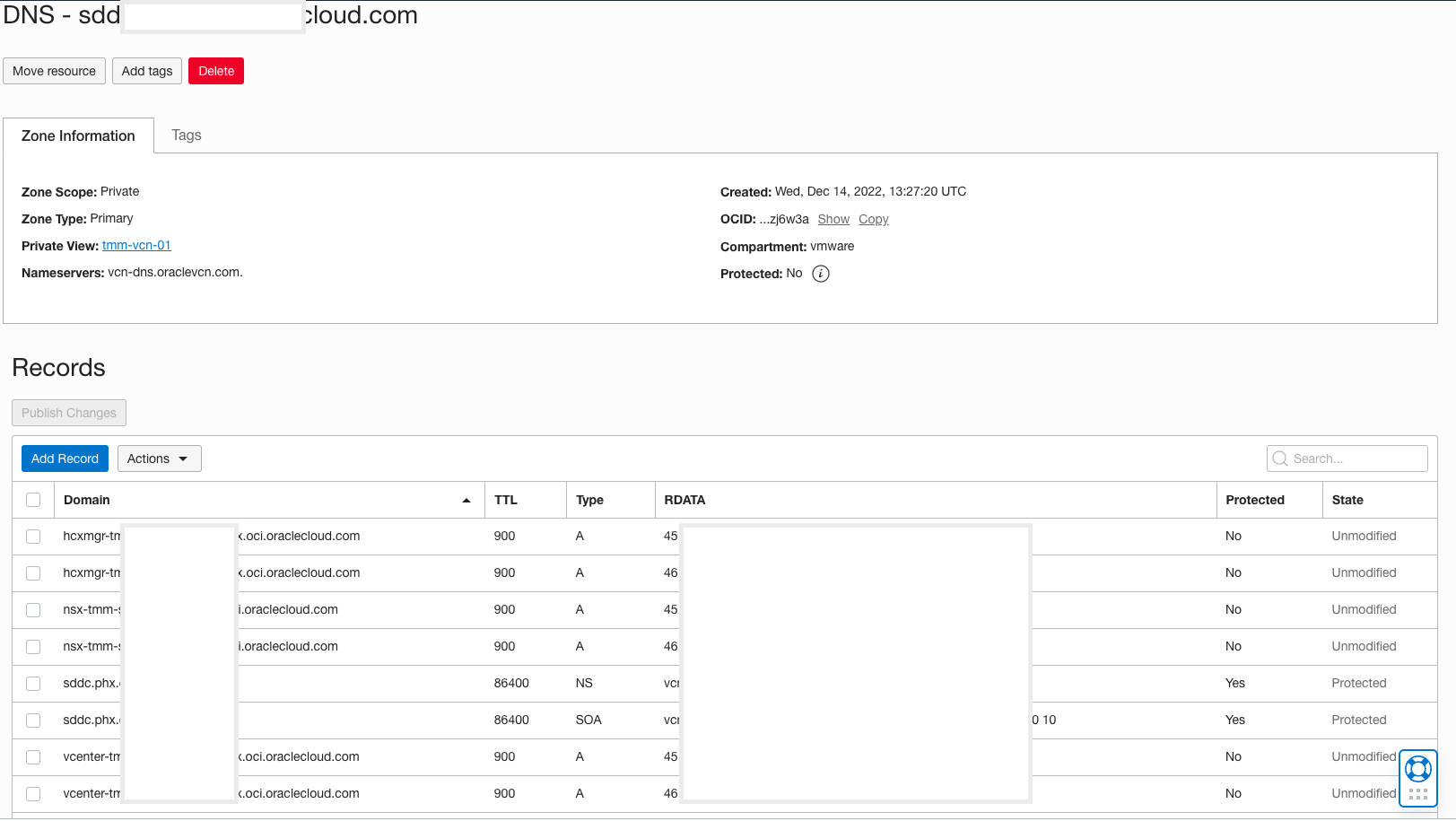
Before getting into the implementation details of configuring the conditional DNS forwarder, let us review OCI DNS zones in detail. Here, I will take an example of one of my OCVS SDDC lab instances and explain how VMware SDDC appliances, such as vCenter, NSX Manager, and HCX, get their FQDN address from OCI DNS.

As you can see in the above diagram, we have a number of DNS zone under the VCN DNS resolver. Each subnet in the VCN corresponds to its respective DNS zone and stores DNS records belonging to instances deployed in those subnets. Let us learn more about each of these zones and understand the DNS records stored in each of these zones.
- sddc.phx.oci.oraclecloud.com
This zone stores the DNS records of all the VMware SDDC appliances, such as vCenter, HCX, and NSX Manager endpoints.
| FQDN | Type | RDATA |
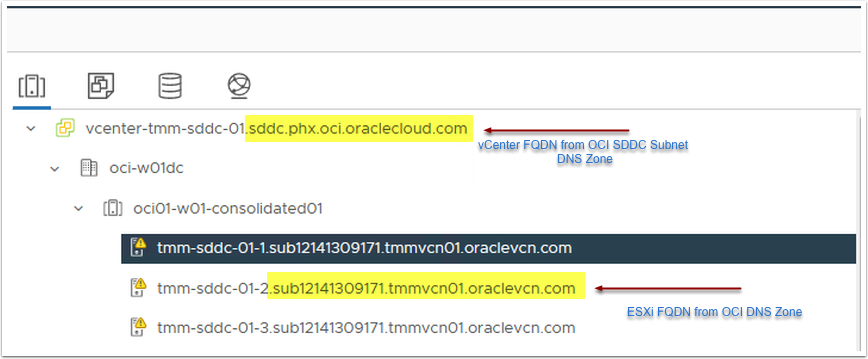
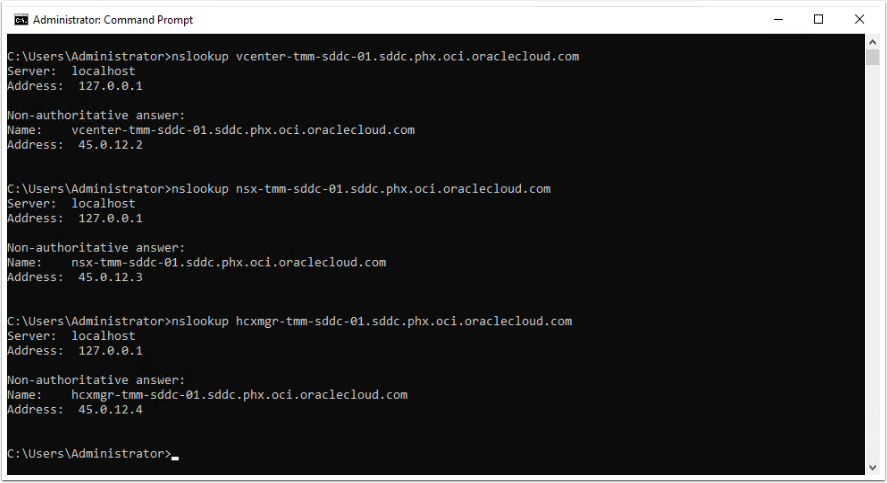
| vcenter-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.2 |
| nsx-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.3 |
| hcxmgr-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.4 |
- sub1241309171.tmmvcn01.oraclevcn.com
This zone stores the DNS records of all the ESXi hosts.
| FQDN | Type | RDATA |
| tmm-sddc-01-1.sub12141309171.tmmvcn01.oraclevcn.com | A | 45.0.8.27 |
| tmm-sddc-01-2.sub12141309171.tmmvcn01.oraclevcn.com | A | 45.0.8.46 |
| tmm-sddc-01-3.sub12141309171.tmmvcn01.oraclevcn.com | A | 45.0.8.71 |
Similarly, there are other OCI DNS zones that stores DNS records of OCI instances and the different service endpoints. We need to configure a conditional DNS forwarder for all the OCI zones that we want to resolve from our custom AD domain. In the case of OCVS SDDC endpoints, we will need to configure conditional DNS forwarders for ‘sddc.phx.oci.oraclecloud.com’ and ‘sub1241309171.tmmvcn01.oraclevcn.com’ in the customer AD DNS server.
CREATE A REVERSE LOOKUP ZONE AND PTR RECORD
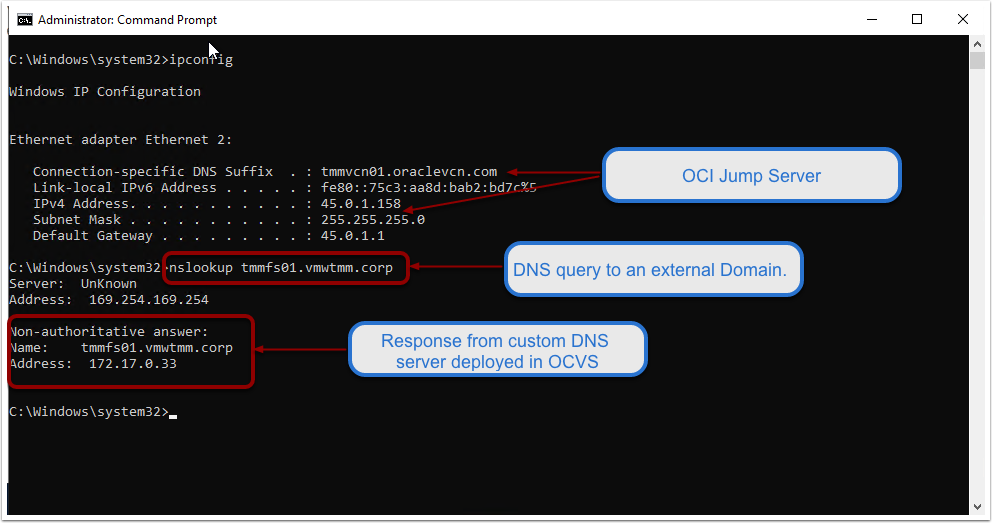
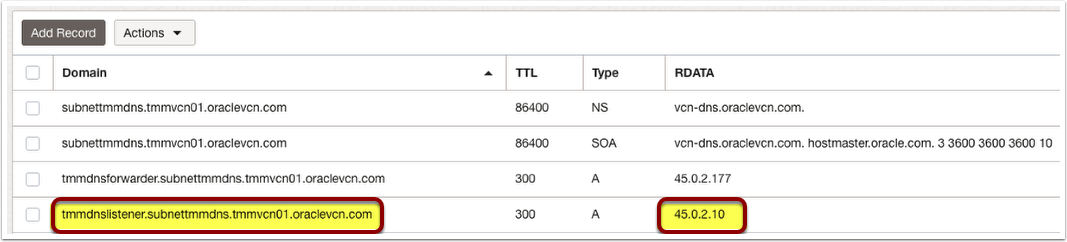
First, we will create a reverse lookup zone for the OCI DNS listener endpoint. In this example, the OCI DNS listener IP address is 45.0.2.10, and its FQDN is ‘tmmdnslistener.subnettmmdns.tmmvcn01.oraclevcn.com’. We will use the reverse lookup zone to create a PTR record so that conditional forwarders can resolve the OCI DNS endpoint.
- Login to the DNS server.
- Explore the DNS application.
- Right-click on Reverse Lookup Zone. And click on New Zone.
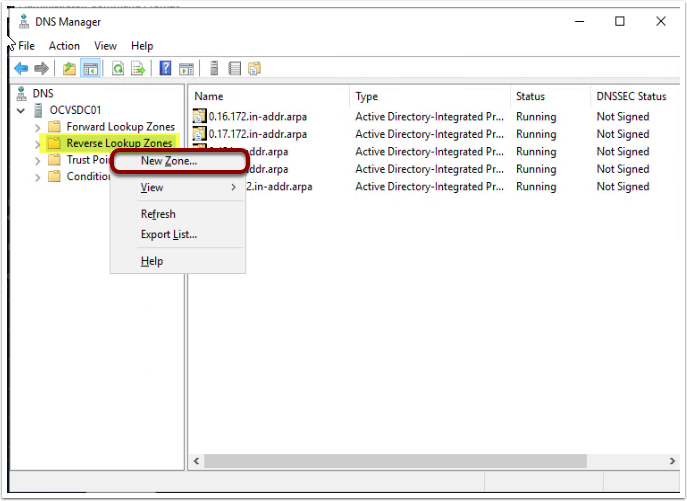
- Select Primary Zone and click Next.
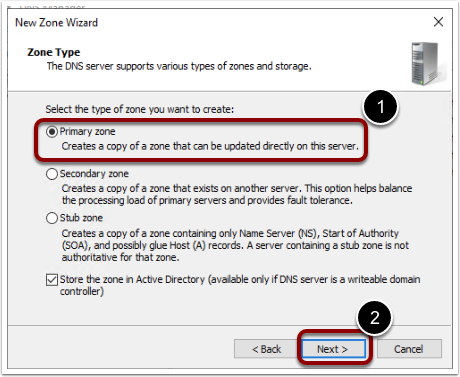
- Select the replication scope as To all DNS servers on domain controllers in this domain: domainname.
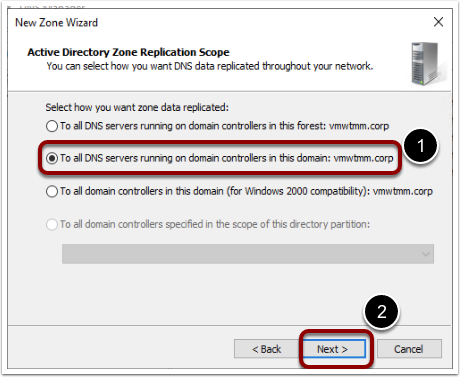
- Select reverse lookup zone as IPv4 reverse lookup zone.
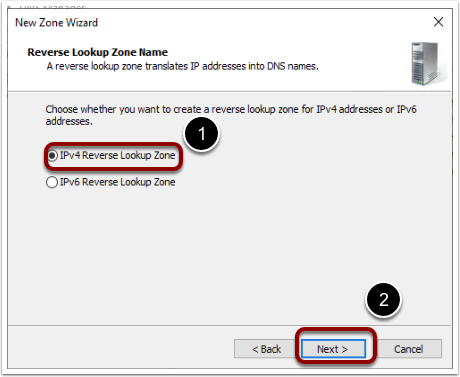
- Provide the network ID.
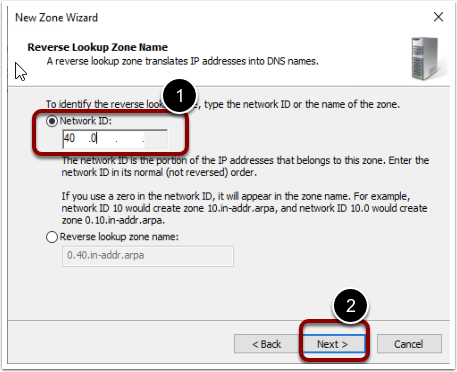
- Enable Allow only secure dynamic updates option.
- Finish.
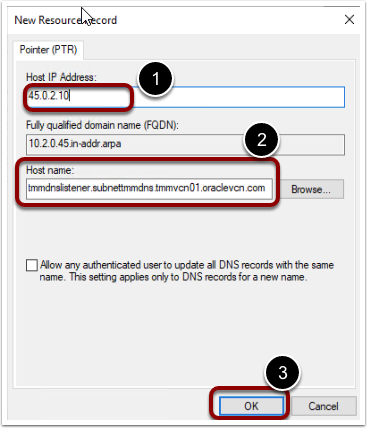
Now create a PTR record for OCI DNS endpoint in the newly created reverse lookup zone.
- Right-click on reverse lookup zone. Select New Pointer (PTR)
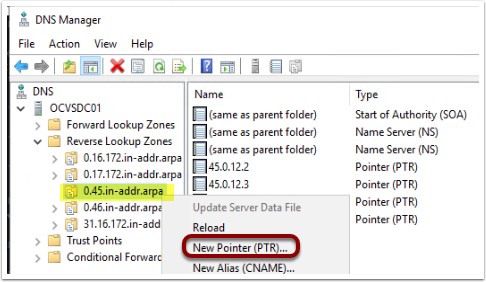
- You can grab the OCI DNS listener endpoint IP address and FQDN from the OCI DNS resolver.
CONFIGURE CONDITIONAL FORWARDER
- Login to the DNS server.
- Explore the DNS application.
- Right-click on the conditional forwarder.
- Select New Conditional forwarder.
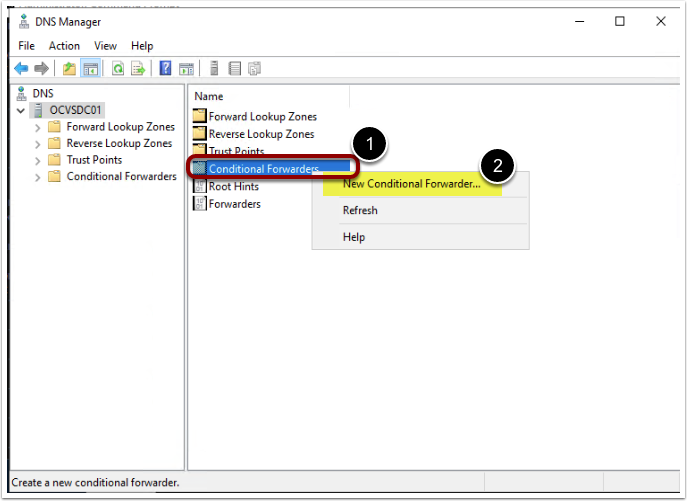
- Provide following details
- DNS zone name: This is the OCI DNS zone that you want to resolve
- Provide OCI DNS Listener IP address. Please note that the first attempt will fail to resolve the IP address and return a failure message <Unable to resolve>, as shown in the picture below. But continue with the process.
- Store this on all the DNS servers in the domain.
- Click OK.
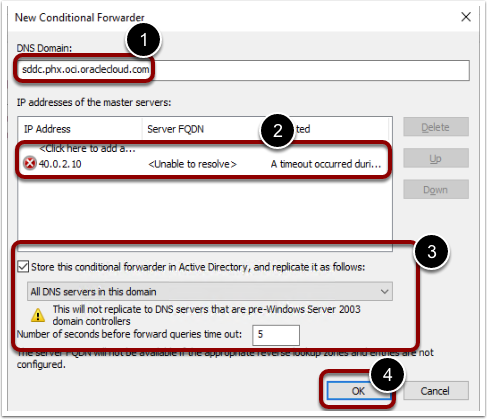
Note:
After finishing this task, Go to conditional DNS forwarder and its properties. Edit the conditional DNS forwarder, and you will see that now the OCI DNS endpoint is able to resolve its IP address. If you are still getting <Unable to resolve> error message, then please verify the reverse lookup zone and OCI DNS endpoint PTR records.
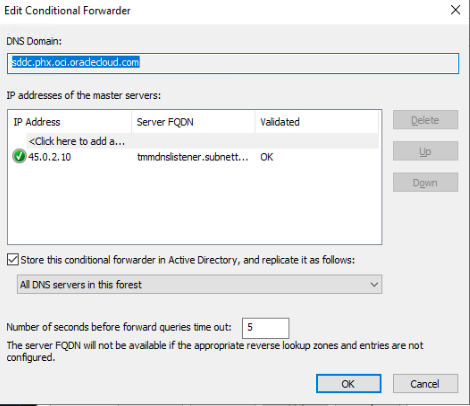
After completion of this step, you should be able to resolve DNS queries related to the ‘sddc.phx.oci.oraclecloud.com’ OCI DNS zone.
| FQDN | Type | RDATA |
| vcenter-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.2 |
| nsx-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.3 |
| hcxmgr-tmm-sddc- 01.sddc.phx.oci.oraclecloud.com | A | 45.0.12.4 |
Test ‘nslookup’ queries on all the SDDC appliances to verify whether the conditional DNS forwarder is working. If it is not working, please ensure that you have the correct routes and firewall settings configured to allow communication between the OCI DNS endpoint and the AD Domain DNS server over port 53.
Repeat the same process for all the OCI DNS zones that you want to resolve from AD Domain DNS Sever.
Conclusion
DNS is an essential part of IT infrastructure. Given the multi-cloud deployment, resolving DNS queries that may belong to different DNS zones and domains becomes even more important. Many VMware solutions such as VMware SRM, HCX, Horizon, and VMware Tanzu require DNS resolution of SDDC appliances such as vCenter and NSX Manager. Conditional DNS forwarders between different DNS zones and domain certainly simplifies DNS management across the multi-cloud implementation.
Authors and Contributors
A list of authors and contributors should be listed here in the following format:
- Jatin Purohit, Sr. Technical Marketing Manager, VMware
Also, I would like to thank and acknowledge Steve Dockar (WW OCVS Field Solution Architect Director) for publishing a wonderful blog post "Its always DNS…" on his blog https://notthe.blog/ . In addition to this, there are some great blog posts explaining different networking use cases on OCVS. Check out the details here.
