Create VMware NSX Networks with PowerCLI on Google Cloud VMware Engine
VMware administrators often rely on PowerShell and PowerCLI to manage a wide range of services throughout the data center: virtual machines, storage, networking, and much more.
VMware NSX is the foundation for virtual networking in every Google Cloud VMware Engine private cloud. For those looking to use scripting to automate typical deployment tasks, such as creating a new network segment, PowerCLI is a perfect fit.
The latest PowerCLI release features a new module that enables you to manage NSX via the Policy API. This new VMware.Sdk.Nsx.Policy module is comprehensive and has access to the full breadth of the NSX API. Because of the powerful capabilities, it may be intimidating to get started.
Essential VMware NSX Configuration for your Private Cloud
To help get you going, a collection of PowerCLI examples that are specifically tailored for managing a GCVE private cloud environment is available. These concepts should also transfer to other NSX-T environments, but certain underlying object naming aligns specifically with GCVE. Regardless, the examples are intended to be a foundation for your own specific automation efforts, so take a copy and modify accordingly!
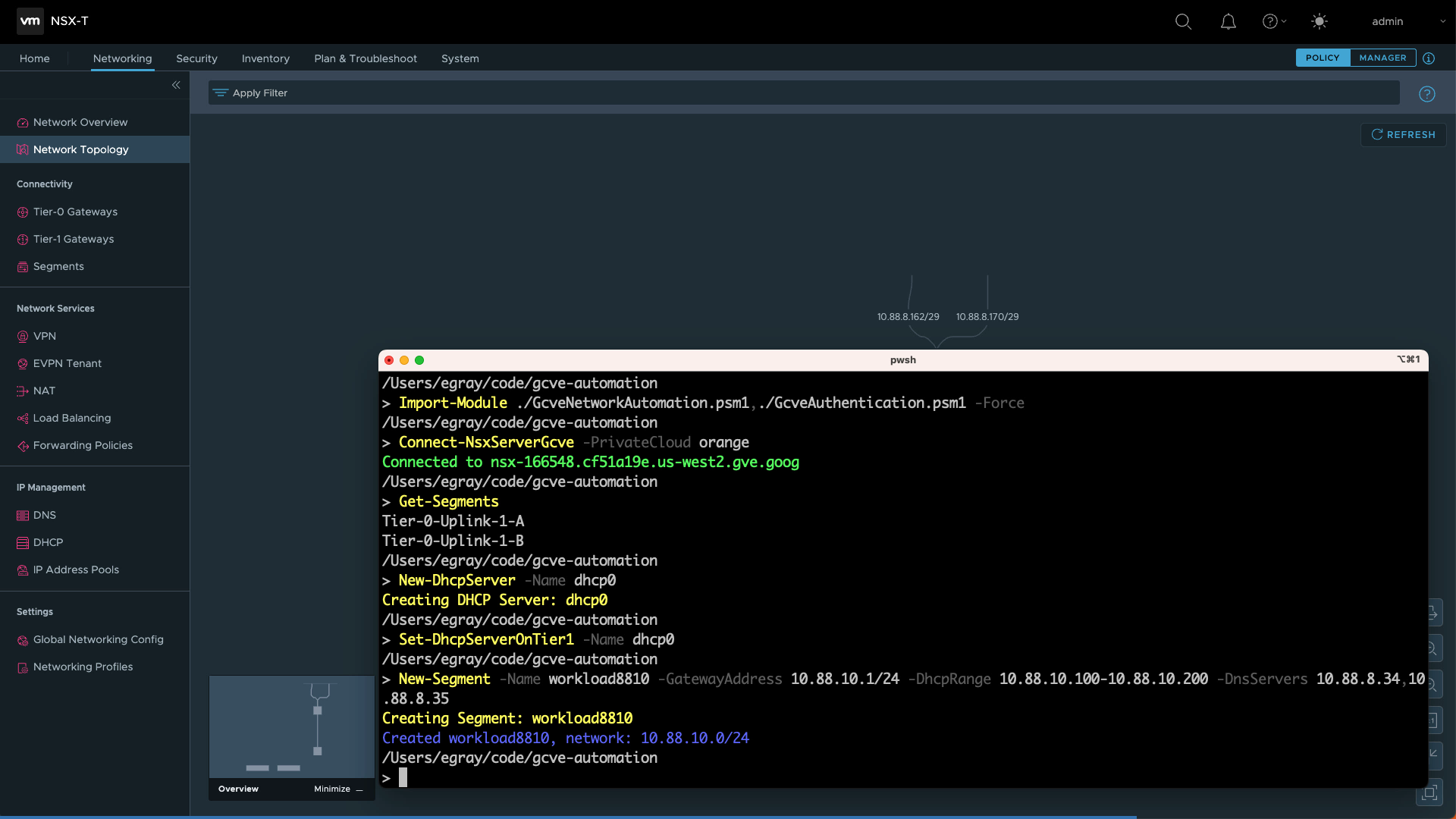
The GitHub repository features a PowerShell module with functions you can use for common tasks: deploy a new DHCP service, attach it to your Tier-1 router, and create new network segments for virtual machines:
Import-Module ./GcveNetworkAutomation.psm1, ./GcveAuthentication.psm1 -Force
Connect-NsxServerGcve -PrivateCloud orange
New-DhcpServer -Name dhcp0
Set-DhcpServerOnTier1 -Name dhcp0
New-Segment -Name workload8810 -GatewayAddress 10.88.10.1/24 `
-DhcpRange 10.88.10.100-10.88.10.200 `
-DnsServers 10.88.0.2, 10.88.1.2 `
-DomainName multicloud.internalIntegrated Google Cloud Authentication
As is the case with most APIs and services, authentication is necessary to manage and configure NSX. You can use the default Connect-NsxServer cmdlet, which accepts the typical parameters of server address, username, and password to create a secure session to the NSX endpoint. But there is an additional capability for use with your Google Cloud VMware Engine private cloud that reduces effort while improving security.
The optional authentication module features a command called Connect-NsxServerGcve that takes advantage of new GCVE automation capabilities for integrated access to both NSX and vCenter endpoints. Using this technique, admin credentials are fetched automatically with the gcloud CLI, helping you to keep sensitive passwords secure by not embedding them inside scripts.
Here is a short demo of the PowerCLI scripts in action:

Takeaway
By using PowerCLI, VMware administrators can get a new private cloud up and running with one or more network segments without ever signing in to the NSX admin web interface!
